To meet expectations of stakeholders, safeguarding product and service information, prevent unauthorized access, alterations, use, disclosure and potential losses resulting from natural disasters, earning the trust of customers and suppliers, and ensuring the uninterrupted functioning of critical business operation.
Furthermore, to fulfill commitment to shareholders, the company employs information security management. This approach guarantees the confidentiality, integrity, and availability of crucial information assets, while also ensuring compliance with pertinent laws and regulations.
Information Security Organization
We have established the information security team, led by the director of the general management office as the convener. This role encompasses information security risk management and performance target assessments. The head of the information department assumes the position of director-general within the
team, responsible for the planning and execution all information security management tasks. Additionally, they present the actual outcomes of information security performance targets to the convener through meetings. Representatives from each unit serve as committee members, supporting the Director-General in the implementing of information security initiatives.
Information Security Policy
To enhance information security management, ensuring security of data, system, equipment, internet security ,as well as the confidentiality, completeness, usability and legality of information assets. This also involves compliance with the stipulations of applicable laws, regulations and contracts, guarding against
both internal and external deliberate or inadvertent threats. We aspire for each employee to adhere to the following expectation:
- Maintain the confidentiality and integrity of information assets.
- Ensure data access is regulated based on departmental functions.
- Sustain the operational status of information systems.
- Prevent unauthorized modification or use of materials and systems.
- Regularly conduct information security audits to ensure its continued safety.
- The company’s information system should establish offsite backups in accordance with risk levels, thereby guaranteeing the security of information data.
- Given the diverse utilization of the internet, continuously enhance security measures to mitigate threats.
Information Security Guidelines
Our information department assumes full responsible for information security. This entails drafting information security policy, formulating plans for the implementation of information security protection, as well as promoting and executing information security policies. In a bid to counteract diverse internal and external information security threats, the company employ a range of s information security measures to enhance the overall security of the information environment.
- User Rights Management: Users need to be assigned varying access rights based on the security levels.
- Security management of operating system usage rights: The installation of the operating system should adhere to the company regulations and involve joining the company’s network domain for centralized management. The operating system requires regular updates, and anti-virus software should be installed on company mainframes and computers. The scanning engine and virus definitions need to be automatically downloaded and updated daily. User account passwords should be regularly updated and configured.
- Software Security Management: Apart from installing application, utility, and package software necessary for information operations, the installation of other specialized software necessitates separate application and approval prior to installation.
- Firewall Configuration: The firewall should incorporate a filtering mechanism to block access to certain software and URLs, thus averting any impact on network e quality and security.
- Online Communicating Security Management: External VPN (remote) access and internal access (file transfer (FTP), instant messaging (LINE), specialized connection (HTTPS), and other network applications) must be approved by information unit’s director and undergo a review and authorization process.
- System Security Management: Only authorized operators within the Information Unit should be permitted to handle source code storage and revision. Different program execution privileges for users should be established in line with business requirements.
- Off-site Backup Management: Systematic disaster recovery and database backup management protocols should be established.
- Asset Management: Equipment within the computer room and personal computers should be assigned asset numbers and subjected to regular inventory checks.
- Enhancing employee’s awareness of information security through continuous communication and education.
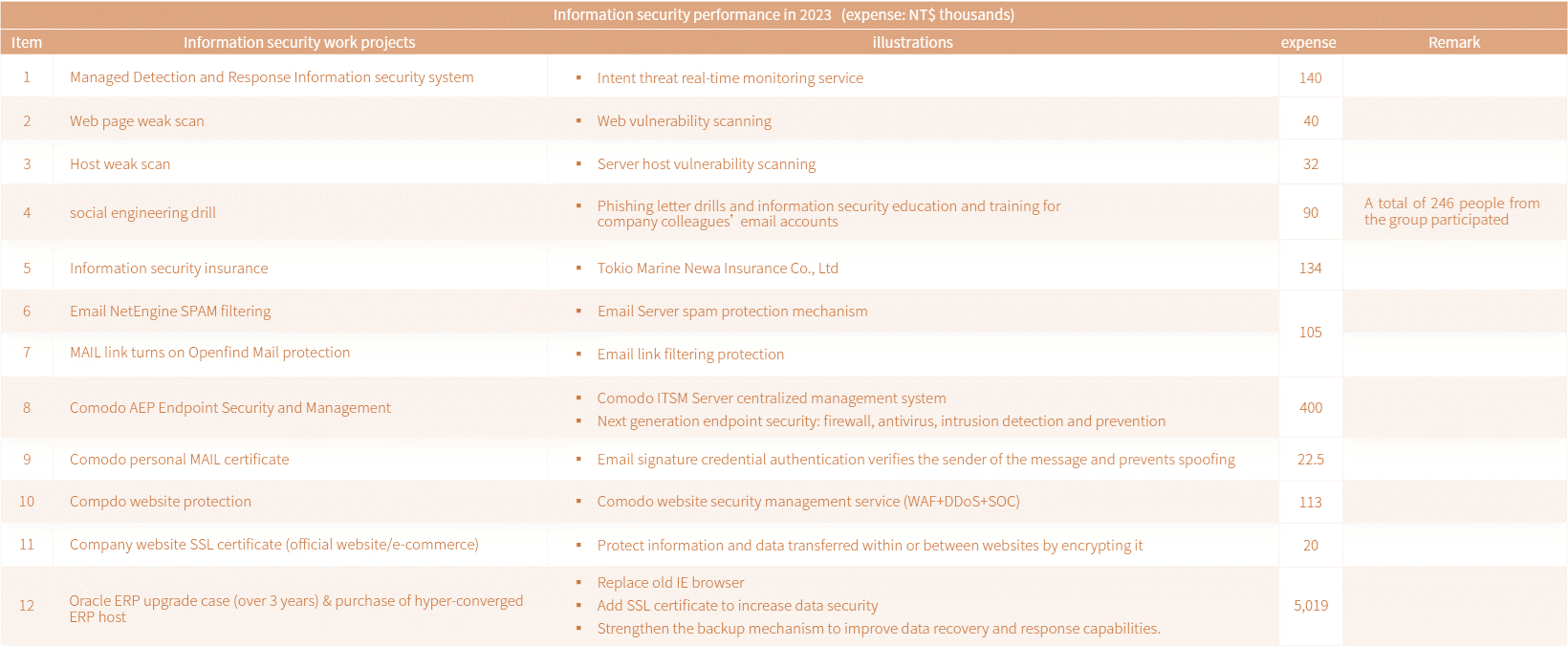
2023 Annual Results
- No major cyber security incidents occurred in 2023.
- The cyber security audit for 2023 has been completed, with no non-compliance issues identified. The audit results show that the information security protection capabilities and infrastructure are controlled and comprehensive.